Introduction to Attack Vectors
What Are Attack Vectors?
An attack vector is any method or pathway through which a cyber attacker gains unauthorized access to a network, system, or device. Attack vectors include vulnerabilities and weaknesses within an organization’s cyber defenses, exploited by hackers to infiltrate systems and compromise data. Understanding attack vectors is essential for effective cyber security because each vector represents a potential pathway for attackers to breach networks and cause harm.
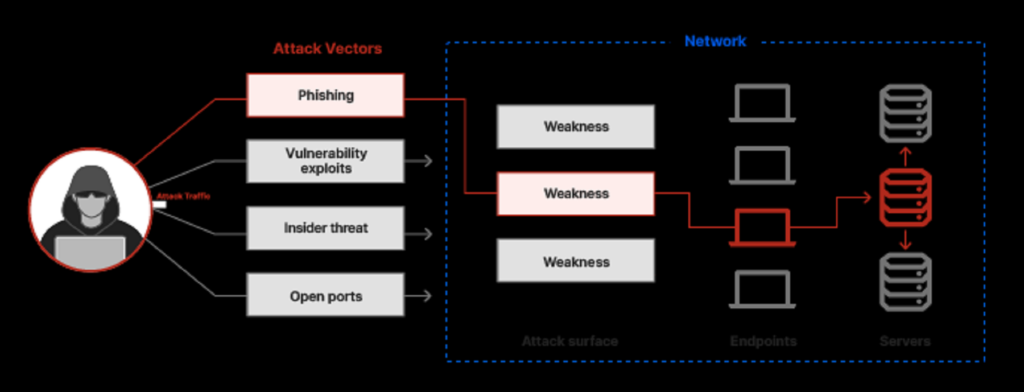
Attack vectors can range from sophisticated malware and ransomware to more direct social engineering tactics like phishing. They leverage both technology weaknesses and human vulnerabilities, making them a persistent threat to businesses of all sizes. The variety and adaptability of attack vectors require organizations to adopt a comprehensive approach to network security that anticipates both current and emerging threats.
Where Attack Vectors Originate
Attack vectors can originate both externally and internally within an organization. External vectors are typically initiated by cybercriminals outside the organization, seeking financial gain, espionage, or the disruption of business operations. These threats often emerge from malicious software, DDoS attacks, and phishing schemes. Meanwhile, internal attack vectors can be introduced by employees, either unintentionally, through actions like clicking on a phishing link, or intentionally, when a malicious insider exploits internal systems.
The rise of the Internet of Things (IoT) and connected devices has broadened the landscape, allowing new avenues for potential threats. Each IoT device, from office cameras to networked appliances, can potentially serve as an entry point for attackers if not properly secured.
Why Attack Vectors Are Critical in Cyber Security
Attack vectors are central to cyber security strategies because they provide insight into potential entry points for attackers. Identifying and mitigating attack vectors help organizations anticipate where breaches may occur and implement measures to defend against them. Effective vulnerability management, coupled with threat intelligence, is crucial for limiting these vectors, as proactive monitoring allows security teams to stay ahead of threats and safeguard sensitive information.
Without understanding attack vectors, organizations risk blind spots that attackers can exploit, leading to data breaches, financial losses, and reputational harm. Regular risk assessments are necessary to keep these vectors in check and maintain a strong security posture.
When Attack Vectors Become a Threat
Attack vectors become an immediate threat whenever there is a lapse in cyber security defenses. For example, failing to update software or enforce multi-factor authentication creates gaps that attackers can leverage. Attack vectors are particularly dangerous when organizations are unprepared for new tactics and technologies used by hackers.
Certain times, such as high-profile events or financial reporting periods, can also increase the likelihood of targeted attacks. Cybercriminals often exploit these occasions, knowing that companies may be focused on other priorities, making them vulnerable to attacks.
How Attack Vectors Are Exploited
Attack vectors are exploited through various tactics, including phishing emails, malicious software, and brute-force attacks, among others. Attackers use these methods to gain entry, escalate privileges, and eventually access sensitive information. For instance, phishing attacks lure victims into clicking on malicious links, while ransomware encrypts data, holding it hostage until a ransom is paid.
Attackers often combine multiple vectors to maximize their reach, such as using social engineering to obtain login credentials and then deploying malware to navigate within a network. Understanding these tactics helps businesses develop targeted cyber security strategies to defend against them.
Who is at Risk from Attack Vectors?
Organizations across all industries are at risk from attack vectors, though businesses with valuable data, such as financial institutions, healthcare providers, and technology companies, are particularly vulnerable. Attackers often prioritize companies that hold sensitive data, such as personal information, financial details, or intellectual property, as these are lucrative targets for exploitation.
Even smaller businesses are at risk, as attackers sometimes view them as easier targets with fewer cyber security resources. The broader public, including individual consumers, can also be affected, as their data may be compromised through company breaches.
Whom Attack Vectors Target Most Frequently
Attack vectors frequently target individuals within an organization who have access to valuable information or systems. Executives, administrators, and other employees with privileged access are often at higher risk of targeted phishing attacks or social engineering scams. Attackers may also target IT departments, recognizing that their access to network infrastructure could allow for greater control if compromised.
As remote work continues, employees working from home are increasingly targeted due to the security limitations of home networks. Attackers exploit the fact that these networks often lack the robust defenses of corporate environments.
1. Phishing and Social Engineering
Overview of Phishing Tactics
Phishing is a method in which attackers impersonate legitimate entities to trick individuals into revealing sensitive information, such as passwords or financial details. This technique often involves fraudulent emails or websites designed to appear authentic. As one of the most common attack vectors, phishing remains a significant threat to cyber security as it preys on human vulnerabilities.
Evolution of Social Engineering Attacks
Social engineering attacks have evolved significantly, with attackers now using more sophisticated tactics, such as spear-phishing and whaling, to target specific individuals within organizations. These methods are personalized, making them harder to detect and more likely to succeed in bypassing security measures.
Best Practices to Defend Against Phishing
Organizations can defend against phishing by implementing security awareness training and encouraging employees to remain vigilant. Using multi-factor authentication, updating software, and monitoring suspicious emails also helps in reducing the success of phishing attacks.
Advanced Anti-Phishing Technologies
Anti-phishing technologies, such as machine learning algorithms, can detect suspicious patterns in emails and alert users before they engage. Advanced solutions include spam filters, URL scanners, and AI-driven analysis, which collectively strengthen an organization’s defenses against phishing.
Real-Life Examples of Phishing Attacks
Real-world phishing attacks highlight the potential damage caused by this vector. High-profile incidents, such as the phishing-related data breaches at major corporations, emphasize the need for robust phishing defenses across all sectors.
2. Malware and Ransomware
Types of Malware Commonly Used in Attacks
Malware is malicious software designed to disrupt, damage, or gain unauthorized access to systems. Types of malware include trojans, spyware, and adware. Each type targets systems differently, making it essential for organizations to adopt comprehensive malware protection strategies.
How Ransomware Attacks Work
Ransomware is a specific form of malware that encrypts data, making it inaccessible to the victim until a ransom is paid. This attack vector has seen a rise in recent years, with attackers targeting both individuals and large corporations, often resulting in massive financial losses and operational disruptions.
Key Protection Strategies for Malware
Employing endpoint protection tools, conducting regular backups, and educating users about suspicious files are effective strategies against malware. Organizations should also ensure vulnerability management is in place to prevent exploitations that lead to malware infections.
Common Malware Delivery Methods
Malware can be delivered through various methods, including email attachments, infected websites, and compromised USB drives. Recognizing these methods is essential in preventing malware from infiltrating networks and causing widespread damage.
How to Recover from Ransomware
In the case of ransomware attacks, having a disaster recovery plan with recent backups is crucial. Organizations should avoid paying ransoms and instead focus on restoring data from backups, which also discourages attackers from targeting other companies.
3. Distributed Denial-of-Service (DDoS) Attacks
Mechanics of a DDoS Attack
A Distributed Denial-of-Service (DDoS) attack involves overwhelming a network or website with traffic, causing it to slow down or crash. Attackers use multiple compromised devices to flood the target with requests, disrupting operations and preventing legitimate access.
Impacts of DDoS on Businesses
DDoS attacks can lead to significant financial and reputational losses, as they disrupt online services and customer experiences. Industries like e-commerce and finance are especially vulnerable, as downtime directly affects revenue and customer trust.
Effective DDoS Mitigation Techniques
Mitigating DDoS attacks involves using load balancers, implementing firewalls, and working with a DDoS mitigation service. These strategies can help redirect and manage traffic during an attack, minimizing the impact on critical services.
Examples of Major DDoS Attacks
Historical DDoS attacks, such as those targeting large-scale companies and government institutions, illustrate the potential scale and consequences of this attack vector. Learning from these incidents helps inform better network cyber security practices.
Building Resilience Against DDoS Attacks
Resilience can be built by designing scalable networks and implementing strong DDoS defense mechanisms. This proactive approach ensures that organizations remain operational even under the strain of a DDoS attack.
4. Insider Threats
Understanding Insider Threat Motivations
Insider threats are security risks posed by employees or contractors within an organization. Motivations range from financial gain to grievances, with both intentional and unintentional actions causing harm. Identifying motivations helps in developing preventive network security measures.
Types of Insider Threats (Malicious vs. Negligent)
Insider threats are classified as malicious or negligent. Malicious insiders intentionally abuse access, while negligent insiders inadvertently cause harm through actions like mishandling data. Both types require different defense strategies.
Strengthening Internal Defenses
Implementing access controls, monitoring network activity, and establishing a strong organizational culture are effective in mitigating insider threats. By restricting access to sensitive information, companies can reduce the likelihood of both accidental and intentional breaches.
Detecting Early Signs of Insider Threats
Monitoring for early signs, such as unusual access patterns or data transfers, can help detect insider threats before they escalate. Security Information and Event Management (SIEM) tools aid in identifying suspicious behavior.
Case Studies of Insider Threat Incidents
Real-life examples of insider threats underscore the necessity for internal security measures. Learning from incidents where insiders compromised data emphasizes the need for vigilance and internal controls.
5. Weaknesses in IoT and Connected Devices
IoT Security Vulnerabilities
The rapid growth of IoT devices has introduced new security challenges. Weak passwords, unpatched software, and default settings create vulnerabilities in IoT networks, making them attractive targets for attackers seeking entry points.
Common Attack Vectors in Connected Devices
Attackers exploit IoT weaknesses to gain access to larger networks. Common methods include botnet attacks and using insecure IoT devices as entry points, allowing attackers to move laterally through an organization’s network.
Securing IoT Environments
Securing IoT environments involves changing default passwords, updating firmware regularly, and segmenting networks to limit access. These practices are essential for protecting IoT devices and preventing them from becoming attack vectors.
Notable IoT Security Incidents
Recent IoT security incidents reveal the potential risks posed by connected devices. High-profile attacks on vulnerable devices underscore the need for strict security measures in IoT deployments.
Future Challenges in IoT Security
As IoT adoption grows, future challenges include managing vast networks of devices and addressing evolving threats. Staying ahead of these challenges is essential for maintaining cyber security as IoT technology advances.
Conclusion
Summary of Key Attack Vectors
This article discussed five critical attack vectors that pose significant risks in 2024: phishing, malware, DDoS, insider threats, and IoT vulnerabilities. Understanding these vectors enables businesses to strengthen defenses and protect against evolving threats.
Importance of Proactive Defense Measures
Proactive security measures, such as continuous monitoring and vulnerability management, are crucial for defending against attack vectors. Organizations must stay vigilant, recognizing that each vector represents a potential pathway for attackers.
Final Thoughts on Future Cyber Security Trends
The cyber security landscape will continue to evolve, with new attack vectors emerging as technology advances. Organizations must adapt to these changes, employing comprehensive strategies that protect against both current and future threats.



