Introduction to Cyber Security Services
Why Cyber Security Services are Vital for Businesses
In today’s digital landscape, cyber security services have become crucial for safeguarding businesses against increasing threats, including cyber security breaches, phishing, and ransomware. Organizations of all sizes are vulnerable to these attacks, which target sensitive data, disrupt operations, and damage reputation. By investing in specialized security services, companies can enhance their defenses, proactively address threats, and maintain operational continuity even in the face of complex cyber challenges.
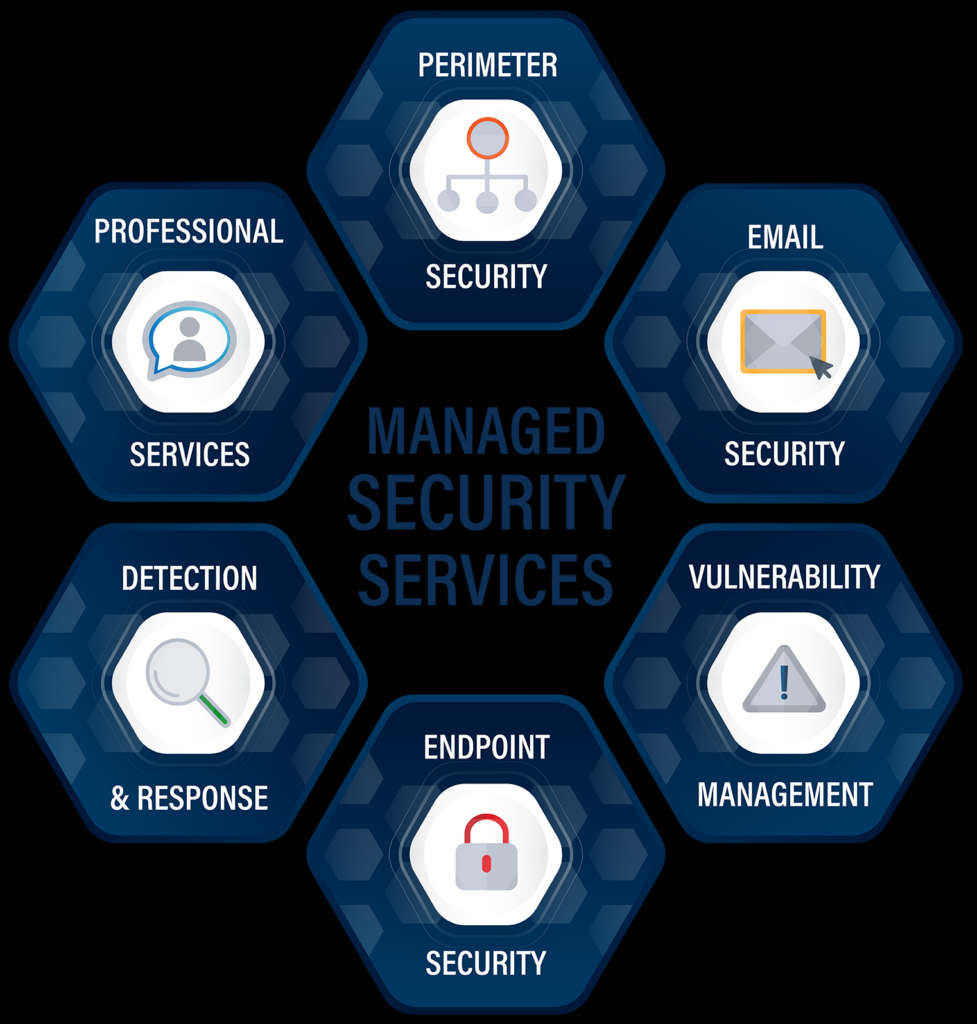
Businesses cannot rely solely on in-house teams to manage the extensive and sophisticated range of modern threats. Cyber security services provide access to expertise, tools, and resources that strengthen security posture beyond what internal teams can typically achieve. These services help ensure compliance with data protection regulations and build resilience against potential attacks, making them an invaluable asset in the current cyber landscape.
Understanding the Evolving Digital Threat Landscape
The digital threat landscape evolves rapidly, with attackers constantly developing new techniques to infiltrate corporate systems. Cyber security threats have become more complex, with emerging tactics like social engineering, phishing scams, and zero-day exploits putting companies at risk. The rise of cloud adoption, remote work, and Internet of Things (IoT) devices has further expanded the attack surface, creating new vulnerabilities for cybercriminals to exploit.
Recognizing these shifts allows businesses to adopt proactive defenses. Cyber security services stay updated on emerging threats, offering continuous threat intelligence, vulnerability assessments, and compliance management to keep organizations secure. By understanding the evolving landscape, companies can protect sensitive information, ensure regulatory compliance, and maintain the trust of their stakeholders.
Building a Strong Digital Defense Strategy
Establishing a robust digital defense strategy involves selecting a combination of cyber security services tailored to the organization’s unique needs. Effective strategies typically include managed security services, threat monitoring, incident response, vulnerability management, and compliance services. Each service strengthens a specific aspect of security, allowing businesses to address both internal and external risks comprehensively.
A strategic approach to digital defense ensures not only prevention but also rapid recovery from cyber incidents. By creating a comprehensive security plan, businesses can protect critical assets, maintain operational stability, and establish a reputation for reliability. This holistic approach demonstrates a commitment to data protection and enhances the organization’s resilience against a range of cyber threats.
Managed Security Services
What Managed Security Services Offer
Managed Security Services (MSS) involve outsourcing security functions to an external provider who delivers ongoing protection and risk management. Services include threat monitoring, firewall management, network security, and incident response. MSS offers businesses peace of mind by ensuring their digital assets are continuously protected and that threats are detected and addressed before they escalate.
Managed security providers leverage cutting-edge tools and methodologies to deliver advanced threat detection, response, and compliance solutions. MSS providers’ expertise in handling a variety of cyber risks makes them valuable partners, particularly for organizations with limited in-house resources.
Benefits of Outsourcing Security Management
Outsourcing security management provides several key advantages, including cost efficiency, access to skilled professionals, and scalability. Many businesses lack the budget or personnel to build a complete internal security team. Managed security services offer a practical alternative, providing high-quality protection without the overhead costs associated with hiring, training, and retaining in-house security staff.
Managed security providers offer access to state-of-the-art technology, giving businesses the ability to secure their operations with advanced tools and real-time monitoring. Furthermore, MSS can scale with the business, allowing organizations to adjust their level of protection as they grow or face new threats.
Key Providers and Their Offerings
Several top providers in managed security services include Cisco, IBM Security, and Symantec (Broadcom), each offering specialized solutions tailored to various industries. Cisco provides solutions like Managed Threat Defense for advanced threat detection and response, while IBM’s QRadar platform combines AI-driven threat intelligence with data analysis. CrowdStrike offers endpoint protection known for its effectiveness against malware and ransomware.
Selecting a provider depends on factors such as the organization’s industry, budget, and specific security requirements. Evaluating each provider’s experience, tools, and scalability ensures that the selected partner aligns with the company’s security objectives.
Threat Intelligence and Monitoring
Importance of Continuous Threat Monitoring
Threat monitoring is essential for identifying and mitigating risks in real-time. It involves constant observation of network activity to detect unusual patterns or suspicious behavior that may indicate an attack. Threat monitoring allows companies to react swiftly to potential breaches, stopping incidents before they escalate into severe security issues.
Organizations that leverage continuous monitoring services gain proactive defense against threats. Real-time threat intelligence offers businesses insights into vulnerabilities, enabling them to adjust their defenses and stay one step ahead of cybercriminals.
Tools and Techniques in Threat Intelligence
Threat intelligence tools such as FireEye, CrowdStrike, and Palo Alto Networks help businesses gather and analyze data on emerging threats. These tools employ advanced machine learning and big data analytics to detect attack patterns and forecast potential risks. By using these insights, companies can make data-driven decisions that enhance their cyber security strategies.
Access to threat intelligence equips businesses with knowledge about specific threats targeting their industry, enabling them to anticipate and neutralize attacks. By continuously analyzing global threat landscapes, organizations gain a strategic advantage, positioning themselves to respond effectively to potential threats.
How Real-Time Insights Strengthen Security
Real-time insights provide a dynamic advantage, allowing businesses to prioritize high-risk vulnerabilities, allocate resources strategically, and implement timely defenses. With up-to-date information on cyber threats, security teams can adapt their responses, ensuring that preventive measures remain relevant and effective.
Industries dealing with sensitive information, such as finance and healthcare, benefit greatly from real-time threat intelligence. By integrating these insights into their security framework, companies can minimize the likelihood of successful attacks and protect both their assets and reputation.
Incident Response and Recovery Services
Essentials of Effective Incident Response
An incident response service prepares businesses to handle cyber incidents, including data breaches and malware attacks, by providing a structured plan. This plan outlines the steps required to identify, contain, and mitigate security breaches quickly, reducing potential damage and enabling a rapid return to normal operations.
Incident response services are crucial for preventing incidents from spreading across networks and minimizing their impact. A well-developed response plan enables organizations to respond with speed and accuracy, reducing downtime and preserving critical business functions.
Steps to Quick and Comprehensive Recovery
The recovery phase focuses on restoring business operations after an incident. Recovery services include data restoration, system repair, and security adjustments to prevent future attacks. Organizations should have recovery plans that incorporate data backups, system patching, and incident analysis to support fast and effective recovery.
By addressing the vulnerabilities identified during the incident, businesses can strengthen their defenses and reduce the risk of future breaches. Comprehensive recovery not only restores systems but also enhances long-term security.
Building a Resilient Response Framework
A resilient response framework involves regular testing, simulations, and employee training to ensure that the incident response plan remains effective. Organizations should review and refine their response strategies periodically, adapting to new threats and integrating lessons learned from past incidents.
Establishing resilience builds confidence in the organization’s ability to handle cyber incidents effectively. This preparedness minimizes potential disruptions, safeguarding both operations and customer trust.
Vulnerability Assessment and Penetration Testing
Role of Vulnerability Assessments in Prevention
Vulnerability assessments help organizations identify weaknesses in their systems before attackers can exploit them. Regular assessments involve scanning networks, applications, and devices to uncover security gaps. Addressing these vulnerabilities promptly strengthens the company’s defenses and lowers the risk of successful attacks.
By conducting frequent assessments, businesses proactively identify and remediate weaknesses, which is key to maintaining a strong security posture. Preventative assessments are a foundational element of effective cyber security.
How Penetration Testing Identifies Weaknesses
Penetration testing, or ethical hacking, simulates attacks on a company’s systems to identify vulnerabilities. These tests reveal how attackers could potentially infiltrate systems, providing valuable insights into which areas need improvement. Regular penetration testing helps organizations understand and fortify their security architecture.
Penetration testing is essential for organizations with high-security needs, as it verifies the effectiveness of existing defenses. Conducting these tests allows businesses to prioritize improvements, enhancing security by addressing critical vulnerabilities.
Incorporating Regular Assessments for Safety
Integrating regular vulnerability assessments and penetration testing into the organization’s security strategy provides continuous improvement. Routine assessments ensure that new vulnerabilities are identified and remediated, reducing the risk of data breaches. Regular testing and assessments enhance overall security by keeping defenses updated and effective.
By staying proactive, organizations create a safer environment, protecting data, operations, and client trust.
Risk Management and Compliance Services
Ensuring Compliance with Data Regulations
Risk management and compliance services are essential for businesses that handle sensitive data, as regulatory standards like GDPR and HIPAA impose strict requirements. Compliance services ensure that companies follow necessary regulations, preventing legal and financial consequences while protecting customer information.
These services help organizations understand and address regulatory requirements, maintaining compliance and avoiding fines. Compliance services also provide peace of mind for clients, assuring them that their data is handled responsibly.
Managing Security Risks Across the Business
Effective risk management involves identifying and mitigating security risks across the organization. Services in this area focus on assessing vulnerabilities, analyzing potential threats, and implementing controls to minimize risks. By proactively managing risks, companies maintain a secure environment that supports their business goals.
Through risk management, businesses can ensure that they prioritize high-risk areas, address weaknesses, and create a culture of security awareness.
Top Risk Management Tools for Businesses
Several tools, such as RSA Archer and MetricStream, support comprehensive risk management by automating risk assessments and tracking compliance. These tools help businesses monitor risks across their operations, providing data-driven insights to guide security strategies.
Implementing risk management tools enables businesses to address vulnerabilities proactively, ensuring that their digital environment remains protected.
Security Awareness Training Importance of Employee Awareness Programs
Employee awareness is critical to reducing cyber security risks, as human error is a common cause of security incidents. Security awareness training educates employees on recognizing threats, such as phishing emails and suspicious links, and encourages safe digital practices.
Awareness programs empower employees to act as a first line of defense, reducing the risk of breaches caused by social engineering and other manipulative tactics.
Core Components of Effective Training
Effective security training includes understanding cyber security technology and learning to identify potential threats. Programs should cover topics such as strong password practices, secure data handling, and recognizing phishing attempts. Regular training ensures that employees stay informed and vigilant against emerging threats.
A well-rounded program not only enhances knowledge but also fosters a security-first mindset across the organization.
Building a Culture of Security Vigilance
Creating a culture of vigilance involves integrating security awareness into the daily operations of the organization. Employees should understand that security is everyone’s responsibility, and businesses should reinforce this through regular updates and engagement.
When employees are security-aware, they contribute significantly to the organization’s defenses, reducing the likelihood of successful attacks.
Conclusion
Recap of Essential Cyber Security Services
The six critical cyber security services discussed—managed security, threat intelligence, incident response, vulnerability assessment, risk management, and security awareness training—form a comprehensive defense against modern threats. Each service addresses unique aspects of security, allowing businesses to protect their digital assets, operations, and reputation.
Strengthening Digital Defense with the Right Services
Selecting the right cyber security services provides businesses with the tools to respond proactively to emerging risks. By adopting a multi-layered security strategy, organizations can maintain a strong defense and prevent costly incidents.
Embracing a Proactive Approach to Cyber Security
Embracing a proactive approach to security positions businesses for success in a digital-first world. Regular assessments, training, and monitoring create a resilient infrastructure that withstands evolving threats, safeguarding both the organization and its clients.



