Red Team Assessment: 6 Proven Methods to Detect Vulnerabilities
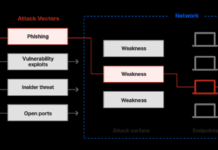
Introduction to Red Team Assessments What is a Red Team Assessment? A Red Team Assessment is a strategic, in-depth security evaluation that simulates real-world cyberattacks to identify an organization's vulnerabilities. Unlike other types of penetra…